Protecting IT and OT Convergence
As IT and OT networks converge, they enable greater production efficiency but also expose OT systems to increased cyber threats. PickPacket Interface Server is designed to protect the communication in both IT and OT/IACS domains.
Protect your IT and OT now with PickPacket
PickPacket Interface Server: First Line of IT/OT Defense
In today’s interconnected industrial environment, cybersecurity is crucial to safeguarding Industrial Automation and Control System (IACS) networks and ensuring continuous operations.
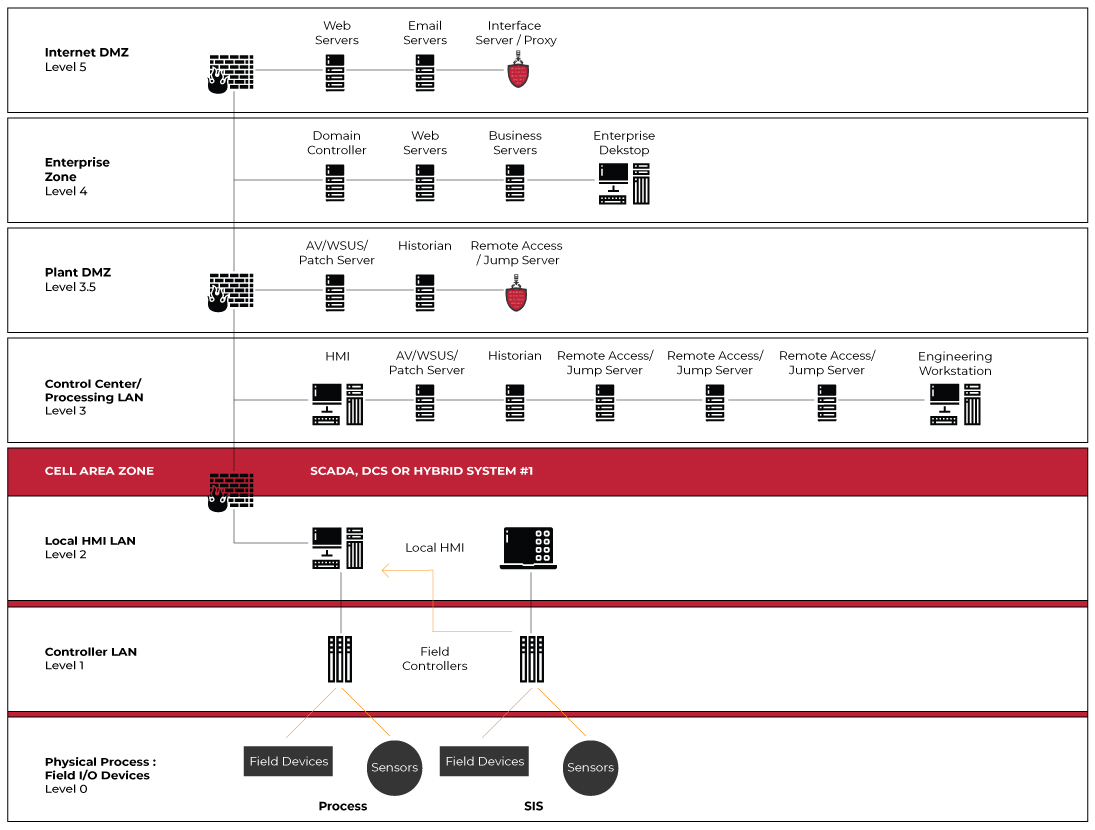
PickPacket Interface Server (PPIS) is engineered to enhance network segmentation, acting as a proactive first line of defense for IT and OT security teams.
It delivers a comprehensive solution that supports compliance with IACS security standards, including ISA99 and ISA/IEC 62443-4-1, while integrating smoothly into the Purdue Enterprise Reference Architecture (PERA) or any network framework.
- Proactive Defense: Acts as the first line of protection against IT/OT security threats.
- Deep Packet Inspection & Intelligent Filtering: Inspects traffic with criteria based on informed decisions and thorough packet validation.
- Load-Balanced Nodes: Distributes heavy connection loads to maintain high performance and reliability.
- Blueprint Protection: Masks and safeguards critical technology architecture from unauthorized discovery.
- Centralized Encryption Management: Handles encryption certificates across the entire infrastructure with Post-Quantum Cryptography (PQC) ready.
IT Visibility for Proactive Defence
Web Application Firewall
Protect your web applications from cyber threats with our advanced Web Application Firewall (WAF). It inspects incoming traffic, blocks malicious requests, and prevents attacks such as SQL injection, cross-site scripting, and other vulnerabilities. Designed for enterprise IT systems, it ensures business critical applications remain secure without affecting performance.
DAST and SAST Scanning
Identify vulnerabilities in your applications during runtime. Our combined Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST) scans help detect security flaws early, prevent potential exploits. Our Data Leak Protection solution monitors, detects, and blocks confidential information from leaving your network, ensuring compliance and safeguarding critical business assets.
Load Balancing Between Nodes
Distribute traffic intelligently across multiple sites to ensure high availability and reliability. Our load balancing solution optimises resource utilisation, prevents bottlenecks, and maintains uninterrupted access to applications, supporting seamless operations across your IT infrastructure.
Bandwidth Management
Control and prioritise network traffic to ensure optimal performance for mission critical applications. Bandwidth management allows you to allocate resources effectively, maintain smooth communication, and reduce the risk of network congestion affecting business operations.
OT Security Made Simple
Deep Packet Inspection
Industrial networks face constant threats targeting system and network vulnerabilities. Our Deep Packet Inspection is designed specifically for Industrial Automation and Control Systems (IACS), ensuring malicious traffic is detected without disrupting operations.
Network Segmentation and Zone Protection
Protect your critical control systems by separating networks into security zones. By controlling how external users and remote connections access Levels 0–2 of your ISA-95 environment, you reduce the attack surface, contain potential breaches, and ensure cyber threats are stopped before reaching essential systems.
Intrusion Detection and Anomaly Monitoring
Detect threats before they cause damage. Our solution continuously monitors your network and devices for abnormal behaviour such as malware, unauthorised commands, or unusual traffic patterns and logs events seamlessly to your SIEM for full visibility and compliance.
Secure Communication and Encryption
PickPacket Ensure all OT data is protected in transit. Our solution encrypts commands and telemetry, safeguarding integrity and confidentiality while preventing spoofing, eavesdropping, or command injection, in full alignment with IEC 62443 standards.